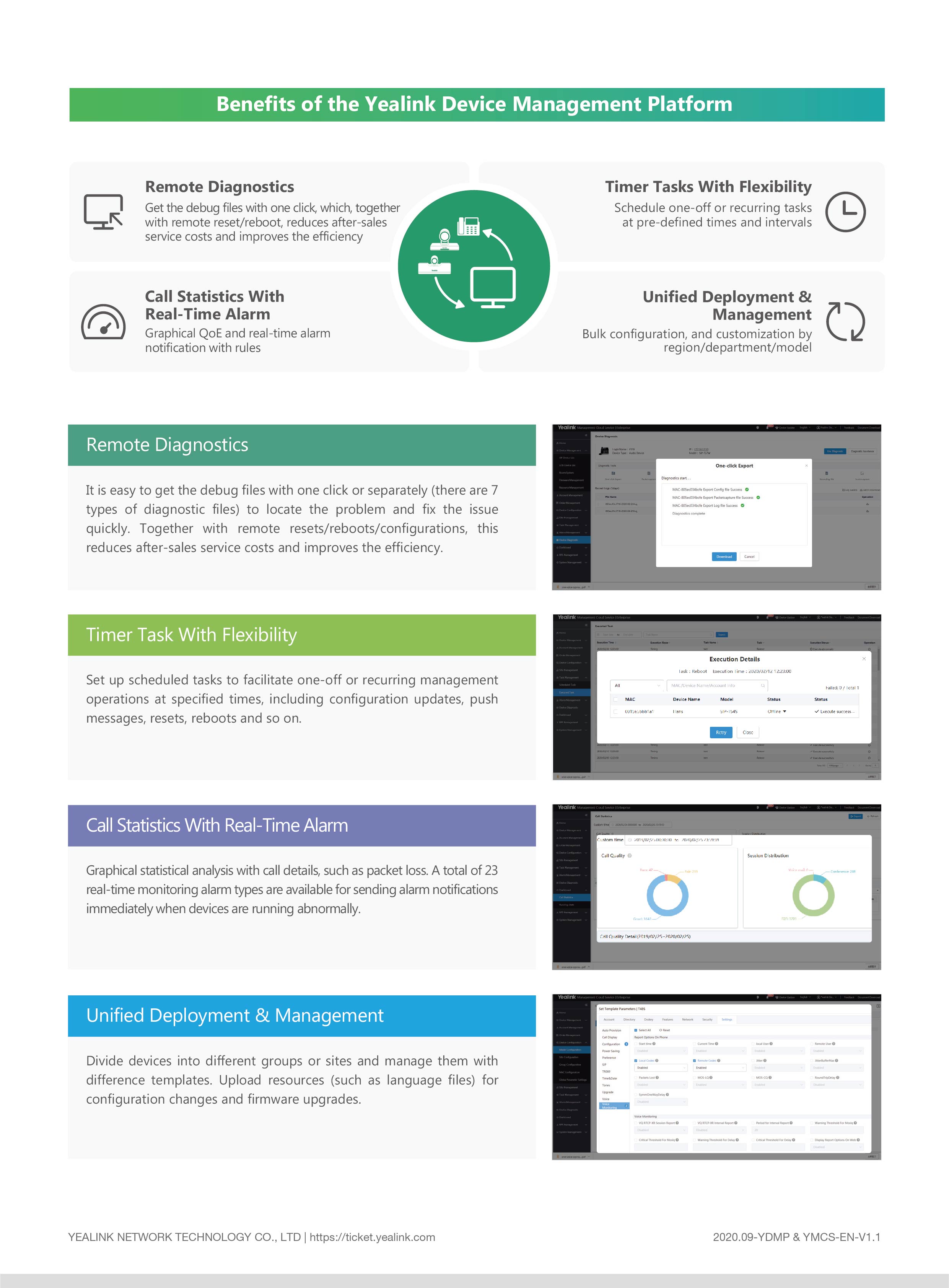
Securely Connect Remote IoT VPC AWS: The Ultimate Guide For Modern Businesses
Hey there, tech-savvy reader! If you're looking to securely connect remote IoT devices to your VPC on AWS, you've come to the right place. In this digital age, IoT security is more crucial than ever. Protecting your data and ensuring seamless communication between devices is not just a luxury—it's a necessity. Let's dive in and explore how you can achieve this without breaking a sweat!
So, why should you care about securely connecting your IoT devices to AWS VPC? Well, imagine this: your company relies heavily on IoT devices to monitor inventory, manage logistics, or even track customer behavior. Now, what happens if someone hacks into your system? Chaos, right? That’s why securing your IoT setup is like locking your house before heading out—it’s essential.
And here’s the kicker: AWS offers some pretty awesome tools and features to make this process smoother than ever. From robust security protocols to scalable infrastructure, AWS has got your back. But hey, let’s not get ahead of ourselves. First, let’s break it down step by step so you can confidently implement this in your own environment.
- Movieuniverse Your Ultimate Guide To Exploring The World Of Movies
- 123movieshdtop Your Ultimate Guide To Streaming Movies Online
Understanding the Basics of Secure IoT Connections
Before we jump into the nitty-gritty, let’s make sure we’re all on the same page. What exactly does it mean to securely connect remote IoT devices to an AWS VPC? Simply put, it’s about creating a safe and reliable connection between your IoT devices and your virtual private cloud (VPC) on AWS. Think of it like building a secure tunnel that only authorized traffic can pass through.
Now, why is this so important? Well, IoT devices are like little data collectors. They gather all sorts of information, from temperature readings to customer preferences. If that data gets into the wrong hands, it could lead to serious consequences. By securely connecting these devices to your VPC, you ensure that only authorized users can access and manage this valuable data.
Key Components of a Secure IoT Connection
Let’s talk about the key components that make a secure IoT connection possible. These are the building blocks that you’ll need to understand before diving into the implementation phase:
- Multimoviesuno Your Ultimate Streaming Hub For Movies And Series
- Movierulzhd The Ultimate Guide To Streaming Movies Online
- Identity and Access Management (IAM): This is like the bouncer at a club. IAM ensures that only authorized users and devices can access your VPC.
- Secure Protocols: Think of these as the language your devices use to communicate. Protocols like TLS and HTTPS ensure that data is encrypted and secure during transmission.
- Network Security Groups (SGs): These act like virtual firewalls, controlling inbound and outbound traffic to your VPC.
- Monitoring and Logging: Keeping an eye on your network is crucial. Tools like AWS CloudWatch help you monitor activity and detect any suspicious behavior.
Setting Up Your AWS VPC for IoT Devices
Alright, let’s get our hands dirty and set up your AWS VPC for IoT devices. The first step is to create a VPC that’s specifically designed to handle IoT traffic. This involves configuring subnets, routing tables, and security groups to ensure a smooth and secure connection.
Here’s a quick rundown of what you’ll need to do:
- Create a new VPC in the AWS Management Console.
- Set up public and private subnets to handle different types of traffic.
- Configure routing tables to direct traffic between subnets and the internet.
- Set up security groups to control access to your IoT devices.
Tips for Optimizing Your VPC Setup
Now that you’ve got the basics down, here are a few tips to optimize your VPC setup:
- Use VPC Endpoints: These allow your devices to communicate with AWS services without going through the public internet, reducing latency and improving security.
- Implement Network ACLs: These act as an additional layer of security, controlling traffic at the subnet level.
- Regularly Update Security Policies: As threats evolve, so should your security policies. Stay up-to-date with the latest best practices.
Securing IoT Devices with AWS IAM
Let’s talk about securing your IoT devices using AWS IAM. IAM is one of the most powerful tools in the AWS arsenal, allowing you to manage access to your resources with precision. By setting up IAM roles and policies, you can ensure that only authorized devices and users can interact with your VPC.
Here’s how you can get started:
- Create an IAM role specifically for your IoT devices.
- Attach policies to the role that define what actions the devices can perform.
- Assign the role to your devices during the onboarding process.
Best Practices for IAM Configuration
When configuring IAM for your IoT devices, keep these best practices in mind:
- Follow the Principle of Least Privilege: Only grant the minimum permissions necessary for your devices to function.
- Use Temporary Credentials: Instead of hardcoding credentials into your devices, use temporary credentials that expire after a set period.
- Monitor and Audit Regularly: Keep an eye on IAM activity to ensure that no unauthorized access occurs.
Implementing Secure Protocols for IoT Communication
Now let’s talk about implementing secure protocols for IoT communication. Protocols like TLS and HTTPS are essential for encrypting data in transit, ensuring that even if someone intercepts your traffic, they won’t be able to decipher it.
Here’s how you can implement these protocols:
- Enable TLS on your IoT devices to encrypt communication.
- Use HTTPS for any web-based interactions with your VPC.
- Regularly update your devices to ensure they’re using the latest protocol versions.
Why Secure Protocols Matter
Secure protocols are crucial because they protect your data from prying eyes. Without them, your IoT devices would be vulnerable to attacks like man-in-the-middle (MITM) and eavesdropping. By implementing these protocols, you’re taking a proactive step towards safeguarding your data.
Managing Network Security with AWS Security Groups
Let’s move on to managing network security with AWS Security Groups. Security groups act as virtual firewalls, controlling inbound and outbound traffic to your VPC. By carefully configuring these groups, you can ensure that only authorized traffic reaches your IoT devices.
Here’s how you can set up security groups:
- Create a new security group in the AWS Management Console.
- Define inbound and outbound rules to specify which traffic is allowed.
- Assign the security group to your IoT devices and VPC resources.
Advanced Security Group Configurations
For those looking to take their security game to the next level, here are some advanced configurations to consider:
- Use Source/ Destination Checks: This ensures that traffic is coming from and going to legitimate sources.
- Implement Stateful Inspection: This allows the security group to track the state of connections, ensuring that only valid traffic is allowed.
- Regularly Review Rules: As your environment changes, so should your security group rules. Keep them up-to-date to reflect current needs.
Monitoring and Logging for IoT Security
Monitoring and logging are essential components of any IoT security strategy. By keeping an eye on your network activity, you can quickly detect and respond to any suspicious behavior. AWS offers several tools to help with this, including CloudWatch and CloudTrail.
Here’s how you can use these tools:
- Set up CloudWatch to monitor metrics like CPU usage and network traffic.
- Use CloudTrail to log API calls and track user activity.
- Configure alerts to notify you of any unusual activity.
Best Practices for Monitoring and Logging
When setting up monitoring and logging for your IoT devices, keep these best practices in mind:
- Set Up Baselines: Establish normal activity levels so you can quickly identify anomalies.
- Regularly Review Logs: Don’t just set it and forget it. Regularly review your logs to ensure everything is running smoothly.
- Automate Where Possible: Use automation to streamline your monitoring and logging processes, saving you time and effort.
Scaling Your IoT VPC Environment
As your business grows, so will your IoT environment. Scaling your VPC to accommodate more devices and traffic is crucial for maintaining performance and security. AWS offers several tools to help you scale efficiently, including Auto Scaling and Elastic Load Balancing.
Here’s how you can scale your IoT VPC environment:
- Use Auto Scaling to automatically adjust the number of instances based on demand.
- Implement Elastic Load Balancing to distribute traffic evenly across your resources.
- Regularly review your scaling policies to ensure they meet your current needs.
Challenges and Solutions in Scaling IoT VPC
Scaling your IoT VPC environment isn’t without its challenges. Here are some common issues and their solutions:
- Latency Issues: Use VPC Endpoints to reduce latency and improve performance.
- Resource Constraints: Optimize your resource usage by regularly reviewing and adjusting your configurations.
- Security Concerns: Implement additional security measures as you scale, ensuring that new devices and resources are properly protected.
Conclusion: Taking Your IoT Security to the Next Level
And there you have it, folks! A comprehensive guide to securely connecting remote IoT devices to your AWS VPC. By following the steps and best practices outlined in this article, you can ensure that your IoT environment is both secure and scalable.
Now, here’s the fun part: take action! Don’t just read this article and forget about it. Implement these strategies in your own environment and see the difference it makes. And hey, if you found this article helpful, don’t forget to share it with your tech-savvy friends. Together, we can make the IoT world a safer place!
Remember, securing your IoT devices isn’t just a one-time task—it’s an ongoing process. Stay vigilant, stay informed, and most importantly, stay secure!
Table of Contents
- Understanding the Basics of Secure IoT Connections
- Setting Up Your AWS VPC for IoT Devices
- Securing IoT Devices with AWS IAM
- Implementing Secure Protocols for IoT Communication
- Managing Network Security with AWS Security Groups
- Monitoring and Logging for IoT Security
- Scaling Your IoT VPC Environment
- Conclusion: Taking Your IoT Security to the Next Level
- Los Moviesru Your Ultimate Destination For Entertainment And Movie Insights
- Up Moviesnet Your Ultimate Destination For Movie Magic

Securely Connect Remote IoT VPC Raspberry Pi AWS Server The Ultimate Guide

Securely Connect Remote IoT VPC AWS Raspberry Pi The Ultimate Guide
Securely Connect Your Remote IoT Raspberry Pi to AWS VPC StepbyStep